What is Cross-Site Scripting?
Cross-site scripting, also known as XSS, is a type of security vulnerability typically found in Web applications. It occurs when a web application gathers malicious data from a user. The data is usually gathered in the form of a hyperlink that contains malicious content. Browsers are capable of displaying HTML content and executing JavaScript. If the application does not escape special characters in the input/output and sends the user input back to the browser, an attacker may be able to launch an XSS attack successfully. Through which malicious files can be executed, session details of a logged-in user can be stolen, or Trojans can be installed.
Types of XSS: The non-persistent (or reflected)
Cross-site scripting vulnerability is the most common type. A non-persistent XSS vulnerability occurs when the data provided by the attacker is immediately executed and a generated page is returned to that user. The persistent (or stored) XSS vulnerability occurs when the data provided by the attacker is saved in the server, and permanently displayed on web pages returned to other users. Another type of XSS attack is DOM Based on XSS. DOM Based XSS (type-0 XSS) is an attack wherein the attack payload is executed as a result of modifying the DOM environment in the victim’s browser.
How to Perform XSS Testing:
- Submitting malicious script through text inputs
- List out all the text input fields [Text box, Text area] in the application.
- Submit simple javascript code, like ‘<script>alert(“XSS”)</script> through each identified text input field.
- If the text box is vulnerable, an alert with the text mentioned in the quotes will be returned.
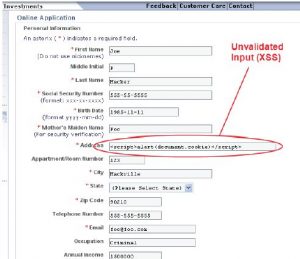
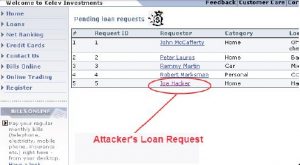
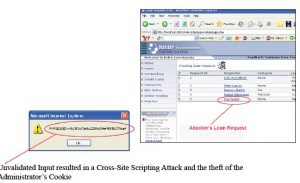
- Submitting malicious script through an application URL
- Modifying the requests using security testing tools like Burp Suite to test for application vulnerability
- Capture the request using the Burp tool
- Append malicious script in the captured request
- ‘Forward’ the modified URL
- Validate the result
How to prevent
XSS attacks are possible mainly because the server is not handling special characters in the output.
There are 2 broad strategies for defeating XSS:
Whitelisting Good inputs
Whitelist: Create a whitelist of characters required by the application. Once the whitelist is ready, the application should disallow all requests containing any character apart from those in the list.
Blacklisting Bad input
Blacklist: The application should not accept any script, special character, or HTML in fields whenever not required. It should escape special characteristics that may prove harmful. Some of the special characters used in the script that must be escaped are <>()[]{}/\*;:=%+^!
Have questions? Contact the software testing experts at InApp to learn more.
