In 2015, a group of security researchers hacked a Jeep, turned its windshield wipers and air conditioners on, and then stopped the functioning of the accelerator. Not only this, they said that they were capable of disabling the engine and the brakes. They could do it by infiltrating the vehicle’s network through manufacturer Chrysler’s in-vehicle connectivity system, Uconnect.
In another instance of Internet of Things security vulnerability, in October 2016, when a hacker exploited a loophole in a specific model of the security camera, more than 300,000 video recorders started to attack many social network websites. This brought down Twitter and other platforms for more than two hours.
The examples above shed light on the vulnerability of IoT and what can happen to IoT systems with poor security apparatus.
According to Statista Research Department, IoT-connected devices worldwide are estimated to reach over 75 billion by the end of 2025. The rising worldwide popularity of Internet of Things usage is unexpected as it brings with it several business advantages across all industries. The advantages include increased efficiency and cost savings among others wherever IoT is used. However, along with varieties of benefits and advantages come several daunting security challenges at all levels.
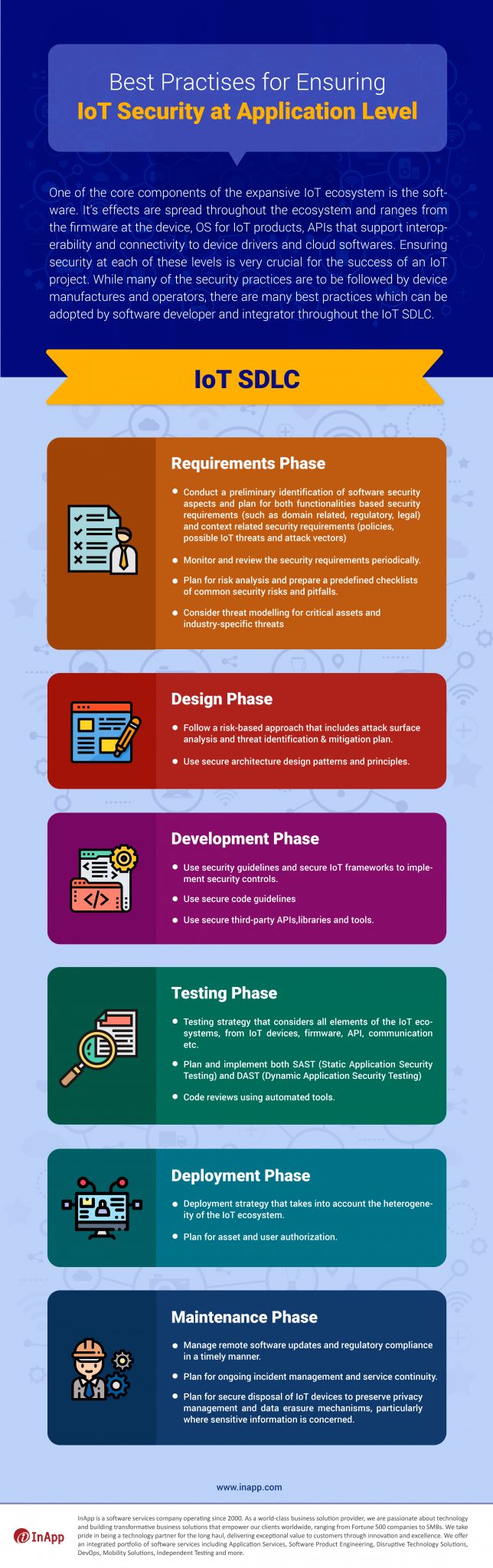
IoT Security Best Practices during IoT Software Development Life Cycle (SDLC)
Requirements Phase
- Conduct a preliminary identification of software security aspects and plan for both functionalities-based security requirements (such as domain-related, regulatory, and legal) and context-related security requirements (policies, possible IoT threats, and attack vectors).
- Monitor and review the security requirements periodically.
- Plan for risk analysis and prepare predefined checklists of common security risks and pitfalls.
- Consider threat modeling for critical assets and industry-specific threats.
Design phase
- Follow a risk-based approach that includes attack surface analysis and threat identification and mitigation plan.
- use secure architecture design patterns and principles.
Development Phase
- Use security guidelines and secure IoT frameworks to implement security controls.
- use secure code guidelines.
- Use secure third-party APIs, libraries, and tools.
Testing Phase
- A testing strategy that considers all elements of the IoT ecosystems, from IoT devices, firmware, API, communication, etc.
- Plan and implement both SAST (Static Application Security testing) and DAST (Dynamic Application Security Testing).
- Code reviews using automated tools.
Deployment Phase
- Deployment strategy that takes into account the heterogeneity of the IoT ecosystem.
- Plan for asset and user authorization.
Maintenance Phase
- Manage remote software updates and regulatory compliance in a timely manner.
- Plan for ongoing incident management and service continuity.
- plan for secure disposal of IoT devices to preserve privacy management and data erasure mechanisms, particularly where sensitive information is concerned.